Technical Program
Final Program and Abstract Book - PDF
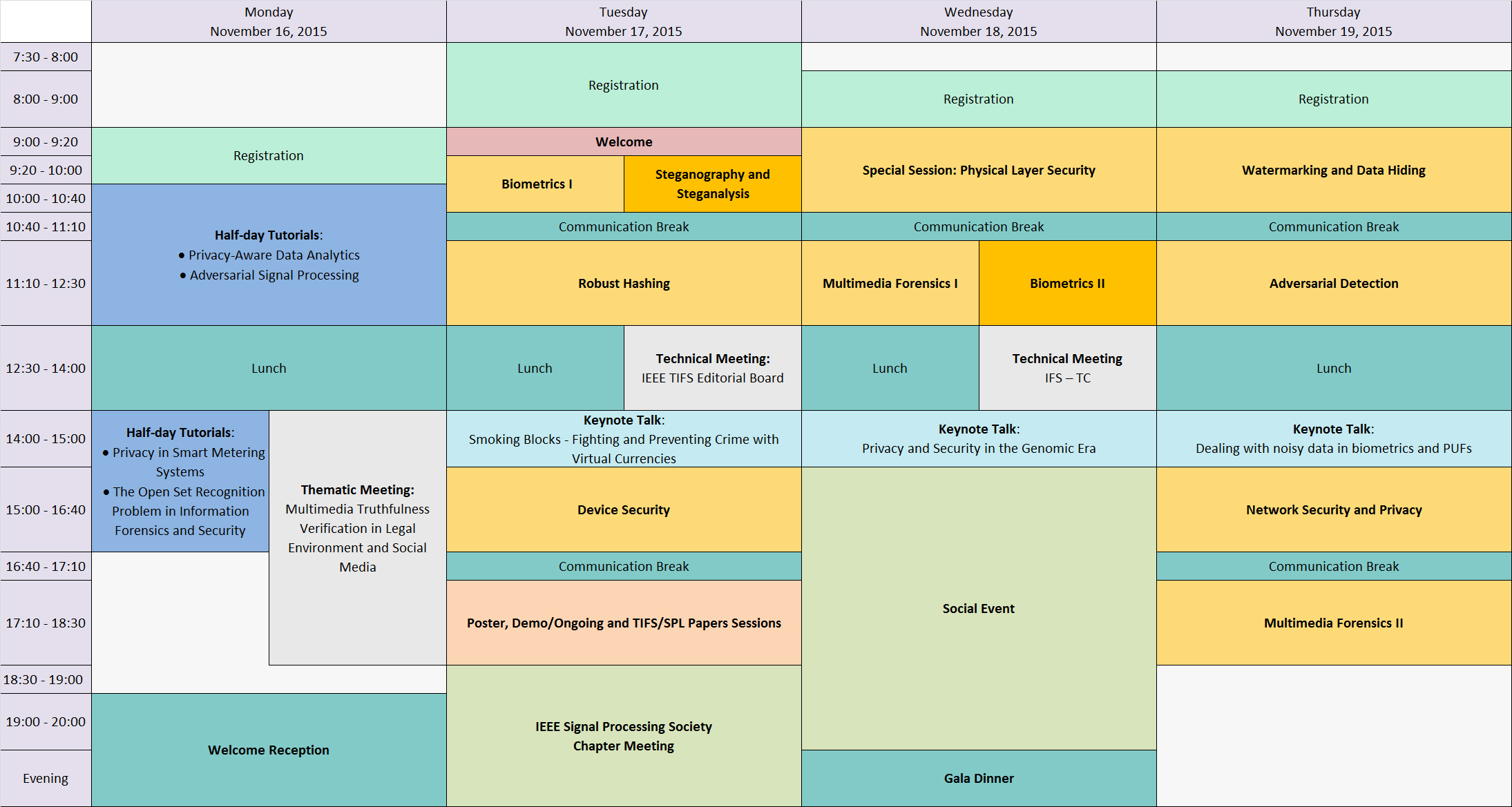
Monday 16 November, 2015
| 10:00-12:30: | Half-day Tutorials |
| Tutorial 1: | Privacy-aware Data Analysi Shantanu Rane |
|
| Tutorial 2: | Adversarial Signal Processing Mauro Barni and Fernando Pérez-González |
| 12:30-14:00: | Lunch |
| 14:00-16:30: | Half-day Tutorials |
| Tutorial 3: | Privacy in Smart Metering Systems Deniz Gunduz and Georgios Kalogridis |
|
| Tutorial 4: | The Open Set Recognition Problem Information Forensics and Security by Walter J. Scheirer and Anderson Rocha |
| 18:30-20:30: | Welcome Reception |
Tuesday 17 November, 2015
| 9:00-9:20: | Aula Magna. Welcome |
| 9:20-10:40: | Aula Magna. Oral Session: Biometrics I |
| 09:20-09:40: | Detection and Segmentation of Latent Fingerprints Xiao Yang, Jianjiang Feng, Jie Zhou and Shutao Xia |
|
| 09:40-10:00: | Local Gabor Rank Pattern (LGRP): A Novel Descriptor for Face Representation and Recognition Abhishek Gangwar and Akanksha Joshi |
|
| 10:00-10:20: | Which Dataset is this Iris Image From? Susan El-Naggar and Arun Ross |
|
| 10:20-10:40: | Update Strategies for HMM-Based Dynamic Signature Biometric Systems Ruben Tolosana, Ruben Vera-Rodriguez, Javier Ortega-Garcia and Julian Fierrez |
| 9:20-10:40: | Aula del Consiglio. Oral Session: Steganography and Steganalysis |
| 09:20-09:40: | Side-Informed Steganography with Additive Distortion Tomas Denemark and Jessica Fridrich |
|
| 09:40-10.00: | A Sequential Method for Online Steganalysis Rémi Cogranne |
|
| 10:00-10:20: | Is Ensemble Classifier Needed for Steganalysis in High-Dimensional Feature Spaces? Rémi Cogranne, Vahid Sedighi, Jessica Fridrich and Tomas Pevny |
|
| 10:20-10:40: | Optimizing Pooling Function for Pooled Steganalysis Tomas Pevny and Ivan Nikolaev |
| 10:40-11:10: | Communication Break |
| 11:10-12:30: | Aula Magna. Oral Session: Robust Hashing |
| 11:10-11:30: | Multiscale Anisotropic Texture Unsupervised Clustering for Photographic Paper Stephane Roux, Nicolas Tremblay, Pierre Borgnat, Patrice Abry, Herwig Wendt and Paul Messier |
|
| 11:30-11:50: | Secure Modular Hashing Abelino Jimenez, Bhiksha Raj, Jose Portelo and Isabel Trancoso |
|
| 11:50-12:10: | Counterfeit Detection Using Paper PUF and Mobile Cameras Chau-Wai Wong and Min Wu |
|
| 12:10-12:30: | Information-Theoretical Limits of Active Content Fingerprinting in Content-based Identification Systems Farzad Farhadzadeh, Frans M. J. Willems and Sviatoslav Voloshynovskiy |
| 12:30-14:00: | Lunch |
| 14:00-15:00: | Aula Magna. Plenary Session |
| Smoking Blocks - Fighting and Preventing Crime with Virtual Currencies Rainer Böhme |
| 15:00-16:40: | Aula Magna. Oral Session: Device Security |
| 15:00-15:20: | Key Search and Adaptation based on Association Rules for Backward Secrecy Kannan Karthik |
|
| 15:20-15:40: | Reliable Secret Key Generation from Physical Unclonable Functions Under Varying Environmental Conditions Onur Günlü, Onurcan Íşcan and Gerhard Kramer |
|
| 15:40-16:00: | Smartphone PINs Prediction using Smartwatch Motion Sensors Allen Sarkisyan and Ani Nahapetian |
|
| 16:00-16:20: | Continuous Authentication and Identification for Mobile Devices: Combining Security and Forensics Soumik Mondal and Patrick Bours |
|
| 16:20-16:40: | Practicability Study of Android Volatile Memory Forensic Research Philipp Wächter and Michael Gruhn |
| 16:40-17:10: | Communication Break |
| 17:10-18:30: | Foyer. Poster Session |
| Rediscovering text in the Yale Martellus Map Roger Easton, Kevin Sacca, Gregory Heyworth, Chet Van Duzer, Kenneth Boydston and Michael Phelps |
||
| TRAP: using TaRgeted Ads to unveil Google personal Profiles Mauro Conti, Vittoria Cozza, Marinella Petrocchi and Angelo Spognardi |
||
| Reconstruction of Smartphone Images for Low Resolution Iris Recognition Fernando Alonso-Fernandez, Reuben Farrugia and Josef Bigun |
||
| Improved Edit Detection in Speech via ENF Patterns Paulo Antonio Andrade Esquef, José Antônio Apolinário Jr. and Luiz Wagner P. Biscainho |
||
| Fast Target Link Flooding Attack Detection Scheme by Analyzing Traceroute Packets Flow Takayuki Hirayama, Kentaroh Toyoda and Iwao Sasase |
||
| Splicebuster: a new blind image splicing detector Davide Cozzolino, Giovanni Poggi and Luisa Verdoliva |
||
| VSig: Hand-Gestured Signature Recognition and Authentication with Wearable Camera Hasan Sajid and Sen-Ching Samson Cheung |
| 17:10-18:30: | Foyer. TIFS/SPL papers |
| A 3D Object Encryption Scheme Which Maintains Dimensional and Spatial Stability Alireza Jolfaei, Xin-Wen Wu and Vallipuram Muthukkumarasamy |
||
| First Quantization Matrix Estimation from Double Compressed JPEG Images Sebastiano Battiato, Giovanni Puglisi, Arcangelo Ranieri Bruna and Fausto Galvan |
||
| Compressed Fingerprint Matching and Camera Identification via Random Projections Diego Valsesia, Giulio Coluccia, Tiziano Bianchi and Enrico Magli |
||
| On the Use of Discriminative Cohort Score Normalization for Unconstrained Face Recognition Massimo Tistarelli, Yunlian Sun and Norman Poh |
||
| A New Biocryptosystem-Oriented Security Analysis Framework and Implementation of Multibiometric Cryptosystems Based on Decision Level Fusion Cai Li, Jiankun Hu, Josef Pieprzyk and Willy Susilo |
||
| On the Continuity of the Secrecy Capacity of Compound and Arbitrarily Varying Wiretap Channels Holger Boche, Rafael F. Schaefer and H. Vincent Poor |
||
| Robust Broadcasting of Common and Confidential Messages over Compound Channels: Strong Secrecy and Decoding Performance Rafael F. Schaefer and Holger Boche |
||
| An investigation of local descriptors for biometric spoofing detection Diego Gragnaniello, Giovanni Poggi, Carlo Sansone and Luisa Verdoliva |
||
| Median Filtered Image Quality Enhancement and Anti-Forensics via Variational Deconvolution Wei Fan, Kai Wang, François Cayre, and Zhang Xiong |
| 17:10-18:30: | Foyer. Demo and Ongoing Works |
| Motion Detection for Surveillance Videos on Encrypted H.264/AVC Bitstream Jianting Guo, Peijia Zheng and Jiwu Huang |
||
| Analysis of Streaming Parameters in Hybrid Video Surveillance Systems Angelo Cardellicchio, Vito Renò and Cataldo Guaragnella |
||
| Visual Bubble Based Privacy Protection Shaoqian Wang, Ying Luo, Wanxin Xu and Samson Cheung |
||
| A surveillance framework for the protection of remote energy facilities using a hybrid multi-class object classification method Georgios Matzoulas, Christos Palaskas, Savvas Rogotis, Dimosthenis Ioanidis and Dimitrios Tzovaras |
||
| Cell-ID Meter App: a Tester for Coverage Maps Localization Proofs in Forensic Investigations Igor Bisio, Giulio Luzzati and Andrea Sciarrone |
||
| Feature-level Multimodal Biometric Authentication in Consumer Mobile Devices Mikhail I. Gofman, Sinjini Mitra, Kevin Cheng and Nicholas Smith |
||
| Efficient Privacy Protection in Video Surveillance by StegoScrambling Natacha Ruchaud and Jean Luc Dugelay |
||
| On Going Work: Group Testing for Nearest Neighbor Search with Privacy Laurent Amsaleg, Teddy Furon, Ahmet Iscen and Li Weng |
||
| Towards a self-recovery scheme for audio restoration Alejandra Menendez-Ortiz , Claudia Feregrino-Uribe , Jose Juan Garcia-Hernandezy and Z. Jezabel Guzman-Zavaleta |
||
| Towards Echo Cancellation With Minimum Error For Robust Reversible Watermarking Alejandra Menendez-Ortiz , Claudia Feregrino-Uribe , Jose Juan Garcia-Hernandezy and Z. Jezabel Guzman-Zavaleta |
||
| Video Recapture Identification by Interframe Correlation Analysis Ernesto Aparicio-Diaz Claudia Feregrino-Uribey Alejandra Menendez |
||
| Macro-social threats connected with anonymity: Ukrainian experience Alexander Kosenkov |
||
| A Forensic Cloud Environment to address the Big Data challenge in Digital Forensics Oteg Tabona and Andrew Blyth |
Wednesday 18 November, 2015
| 9:20-10:40: | Aula Magna. Special Session: Physical Layer Security |
| 09:00-09:20: | Authentication with a Guessing Adversary Farshad Naghibi, Tobias Oechtering and Mikael Skoglund |
|
| 09:20-09:40: | Multicasting with Untrusted Relays: A Noncoherent Secure Network Coding Approach Ta-Yuan Liu, Shih-Chun Lin and Y.-W. Peter Hong |
|
| 09:40-10:00: | Robust PUF based Authentication Andrea Grigorescu, Holger Boche and Rafael Schaefer |
|
| 10:00-10:20: | Worst-Case Secrecy Rates in MIMOME Systems under Input and State Constraints Anne Wolf, Eduard Jorswieck and Carsten Janda |
|
| 10:20-10:40: | Full-Duplex vs. Half-Duplex Secret-Key Generation Hendrik Vogt and Aydin Sezgin |
| 10:40-11:10: | Communication Break |
| 11:10-12:30: | Aula Magna. Oral Session: Multimedia Forensics I |
| 11:10-11:30: | A Second Look at First Significant Digit Histogram Restoration Matthias Kirchner and Sujoy Chakraborty |
|
| 11:30-11:50: | Improved 3D Lighting Environment Estimation for Image Forgery Detection Bo Peng, Wei Wang, Jing Dong and Tieniu Tan |
|
| 11:50-12:10: | General-Purpose Image Forensics Using Patch Likelihood under Image Statistical Models Wei Fan, Kai Wang and François Cayre |
|
| 12:10-12:30: | Image Splicing Detection based on General Perspective Constraints Massimo Iuliani, Giovanni Fabbri and Alessandro Piva |
| 11:10-12:30: | Aula del Consiglio. Oral Session: Biometrics II |
| 11:10-11:30: | Integrating Rare Minutiae in Generic Fingerprint Matchers for Forensics Ram P. Krish, Julian Fierrez and Daniel Ramos |
|
| 11:30-11:50: | The Influence of Segmentation On Individual Gait Recognition Ning Jia, Victor Sanchez, Chang-Tsun Li and Hassan Mansour |
|
| 11:50-12:10: | Some Applications of Verifiable Computation to Biometric Verification Julien Bringer, Hervé Chabanne, Firas Kraïem, Roch Lescuyer and Eduardo Soria-Vazquez |
|
| 12:10-12:30: | Windowed DMD as a Microtexture Descriptor for Finger Vein Counter-spoofing in Biometrics Santosh Tirunagari, Norman Poh, Miroslaw Bober and David Windridge |
| 12:30-14:00: | Lunch |
| 14:00-15:00: | Aula Magna. Plenary Session |
| Privacy and Security in the Genomic Era Jean-Pierre Hubaux |
| 15:00-20:30: | Social Event |
| 20:30: | Gala Dinner |
Thursday 19 November, 2015
| 9:00-10:40: | Aula Magna. Oral Session: Watermarking and Data Hiding |
| 09:00-09:20: | Generalised tally-based decoders for traitor tracing and group testing Boris Skoric and Wouter de Groot |
|
| 09:20-09:40: | A Population of Eagles, Horses, and Moles: Perceptual Sensitivity to Watermark Disparity Coherence Hasan Sheikh Faridul and Gwenael Doerr |
|
| 09:40-10:00: | Automatic Contrast Enhancement using Reversible Data Hiding Suah Kim, Rolf Lussi, Xiaochao Qu and Hyoung Joong Kim |
|
| 10:00-10:20: | Optimum Reversible Data Hiding and Permutation Coding Félix Balado |
|
| 10:20-10:40: | Binary fingerprinting codes - can we prove that someone is guilty?! Marcel Fernandez, Elena Egorova and Grigory Kabatiansky |
| 10:40-11:10: | Communication Break |
| 11:10-12:30: | Aula Magna. Oral Session: Adversarial Detection |
| 11:10-11:30: | Detection Games with a Fully Active Attacker Benedetta Tondi, Mauro Barni and Neri Merhav |
|
| 11:30-11:50: | Impact of Incomplete Knowledge on Scanning Strategy Andrey Garnaev and Wade Trappe |
|
| 11:50-12:10: | On the Effectiveness of Meta-Detection for Countering Oracle Attacks in Watermarking Benedetta Tondi, Pedro Comesaña-Alfaro, Fernando Pérez-González and Mauro Barni |
|
| 12:10-12:30: | Detection of Interest Flooding Attacks in Named Data Networking using Hypothesis Testing Ngoc Tan Nguyen, Rémi Cogranne, Guillaume Doyen and Florent Retraint |
| 12:30-14:00: | Lunch |
| 14:00-15:00: | Aula Magna. Plenary Session |
| Dealing with noisy data in biometrics and PUFs Boris Škorić |
| 15:00-16:40: | Aula Magna. Oral Session: Network Security and Privacy |
| 15:00-15:20: | Trust-based Sybil Nodes Detection with Robust Seed Selection and Graph Pruning on SNS Shuichiro Haruta, Kentaroh Toyoda and Iwao Sasase |
|
| 15:20-15:40: | Achieving Privacy, Efficiency and Fault Tolerance in Aggregate Computations on Massive Star Networks Shantanu Rane, Julien Freudiger, Alejandro Brito and Ersin Uzun |
|
| 15:40-16:00: | Private Data Aggregation with Groups for Smart Grids in a Dynamic Setting using CRT Zekeriya Erkin |
|
| 16:00-16:20: | Decision Tree-based Detection of Denial of Service and Command Injection attacks on Robotic Vehicles Tuan Vuong, George Loukas, Diane Gan and Anatolij Bezemskij |
|
| 16:20-16:40: | Single Relay Selection for Secure Communication in a Cooperative System with Multiple Full-Duplex Decode-and-Forward Relays Binh Nguyen and Kiseon Kim |
| 16:40-17:10: | Communication Break |
| 17:10-18:30: | Aula Magna. Oral Session: Multimedia Forensics II |
| 17:10-17:30: | Fragile Sensor Fingerprint Camera Identification Erwin Quiring and Matthias Kirchner |
|
| 17:30-17:50: | Forensics of High-Quality JPEG Images with Color Subsampling Matthias Carnein, Pascal Schoettle and Rainer Boehme |
|
| 17:50-18:10: | Camera Model Identification Framework Using an Ensemble of Demosaicing Features Chen Chen and Matthew Stamm |
|
| 18:10-18:30: | Identification of pictorial materials by means of optimized multispectral reflectance image processing Lucilla Pronti, Pasquale Ferrara, Francesca Uccheddu, Anna Pelagotti and Alessandro Piva |
For any further information regarding the program, please contact: tpc@wifs2015.org