
Contributed by Dr. Weiqi Luo and co-authors, based on the IEEEXplore® article, “Steganography Embedding Cost Learning With Generative Multi-Adversarial Network”, published in the IEEE Transactions on Information Forensics and Security, 2023.
Introduction
Steganography, the practice of concealing information within digital media, is crucial for information security and forensics. Steganographic security, defined as the ability to evade detection by steganalyzers, is a key metric in modern steganography. Currently, the design of distortion functions plays a vital role in enhancing security, yet traditional methods rely heavily on empirical approaches. The emergence of Generative Adversarial Network (GAN) has introduced a novel way to improve steganographic security. However, existing GAN-based methods [1, 2, 3] mainly optimize the generator while using a single, often weak, steganalyzer in the discriminator. This imbalance limits security performance, as the generator receives insufficient adversarial feedback during training. To address these limitations, we propose Steg-GMAN (Steganography with Generative Multi-Adversarial Network), a novel GAN-based steganographic method designed to learn distortion functions from scratch. More details can be found in the article, and the Steg-GMAN code is available on GitHub.
Proposed Method
As shown in Fig. 1, the proposed Steg-GMAN model retains the typical GAN structure while introducing key enhancements to overcome the limitations of related methods.
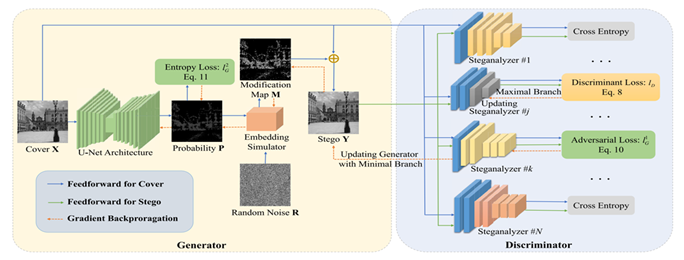
The proposed generator, built on a U-Net architecture, produces an embedding probability map that guides the embedding of secret messages within cover images. Meanwhile, the discriminator integrates multiple steganalyzers, each serving as an independent detector to distinguish generated stego images from cover images. This multi-steganalyzer structure provides stronger adversarial signals, driving the generator to produce stego images that are more resistant to detection.
Moreover, to better train our model, we propose an adaptive training strategy. In each iteration, this strategy updates only the weakest steganalyzer in the discriminator while using the gradient information from the strongest one to update the generator. This approach gradually enhances the overall performance of the discriminator, ensuring a more balanced dynamic between the generator and the discriminator and preventing model collapse.
Experiments
We conducted extensive experiments on multiple datasets, using SZUBase for training and BOSSBase, BOWS2, and ALASKA for testing. Security performance was evaluated with a range of steganalyzers, from traditional methods (e.g., SRM) to advanced CNN-based models (e.g., Xu-Net, Yedroudj-Net, SRNet, and CovNet). Steg-GMAN was benchmarked against one traditional method (HILL [4]) and three GAN-based approaches (ASDL-GAN [1] , UT-GAN [2], and SPAR-RL [3]). Selected comparative results in Table 1 indicate that Steg-GMAN consistently outperforms previous methods. Notably, our approach improves detection error rates by up to 2.77% over SPAR-RL, the best prior GAN-based method, particularly against advanced CNN-based steganalyzers like SRNet.
Table 1. Detection error rate (%) evaluated on five steganalyzers on bossbase dataset. Those values with an asterisk denote the best results in the corresponding cases.
|
Steganalyzer |
Steganographic method |
0.1 bpp |
0.2 bpp |
0.3 bpp |
0.4 bpp |
0.5 bpp |
Average |
|
SRM |
HILL [4] |
43.14 |
37.02 |
31.46 |
26.92 |
22.04 |
32.12 |
|
ASDL-GAN [1] |
43.22 |
34.46 |
29.58 |
24.50 |
19.54 |
30.26 |
|
|
UT-GAN [2] |
44.35 |
38.21 |
32.38 |
28.64 |
24.38 |
33.59 |
|
|
SPAR-RL [3] |
44.94 |
39.15 |
33.29 |
30.34 |
25.33 |
34.61 |
|
|
Steg-GMAN |
45.87* |
40.34* |
34.69* |
30.62* |
26.15* |
35.53* |
|
|
Xu-Net |
HILL [4] |
43.02 |
37.90 |
31.86 |
27.97 |
23.80 |
32.91 |
|
ASDL-GAN [1] |
42.09 |
39.55 |
32.86 |
28.75 |
24.77 |
33.60 |
|
|
UT-GAN [2] |
45.33 |
41.24 |
36.95 |
33.61 |
28.14 |
37.05 |
|
|
SPAR-RL [3] |
46.27 |
42.07 |
38.57 |
35.53* |
29.73* |
38.43 |
|
|
Steg-GMAN |
46.65* |
42.62* |
39.85* |
35.29 |
29.44 |
38.77* |
|
|
Yedroudj-Net |
HILL [4] |
42.97 |
31.33 |
24.42 |
19.54 |
15.62 |
26.78 |
|
ASDL-GAN [1] |
43.43 |
33.46 |
28.17 |
23.12 |
17.85 |
29.21 |
|
|
UT-GAN [2] |
46.90 |
37.21 |
32.03 |
27.14 |
23.18 |
33.29 |
|
|
SPAR-RL [3] |
47.72 |
39.52 |
32.89 |
28.59 |
23.77 |
34.50 |
|
|
Steg-GMAN |
49.91* |
41.57* |
35.21* |
30.85* |
24.15* |
36.34* |
|
|
SRNet |
HILL [4] |
37.02 |
27.21 |
21.85 |
17.33 |
14.80 |
23.64 |
|
ASDL-GAN [1] |
40.03 |
24.48 |
19.25 |
16.23 |
11.87 |
22.37 |
|
|
UT-GAN [2] |
40.09 |
30.82 |
26.31 |
21.92 |
16.45 |
27.30 |
|
|
SPAR-RL [3] |
42.00 |
32.22 |
27.23 |
22.81 |
17.67 |
28.45 |
|
|
Steg-GMAN |
42.99* |
35.57* |
30.77* |
26.15* |
20.60* |
31.22* |
|
|
CovNet |
HILL [4] |
35.33 |
26.28 |
20.91 |
16.10 |
13.52 |
22.43 |
|
ASDL-GAN [1] |
33.78 |
22.34 |
17.86 |
13.74 |
10.64 |
19.67 |
|
|
UT-GAN [2] |
40.03 |
31.73 |
25.29 |
21.97 |
16.29 |
27.06 |
|
|
SPAR-RL [3] |
41.38 |
32.53 |
26.38 |
23.21 |
17.11 |
28.12 |
|
|
Steg-GMAN |
42.20* |
34.75* |
28.42* |
25.38* |
19.31* |
30.01* |
Additionally, further results demonstrated that the adaptive training strategy effectively balances the learning process between generator and discriminator, significantly improving both steganographic security and generalization. Cross-dataset evaluations demonstrated that Steg-GMAN generalizes well, unlike some previous methods such as Backpack, which struggle with cover source mismatch. These results establish Steg-GMAN as the new benchmark for GAN-based steganography, significantly enhancing security in real-world applications.
Conclusion
This paper introduces Steg-GMAN, a novel GAN-based steganographic method that enhances security by integrating multiple steganalyzers and employing an adaptive training strategy. Extensive experiments demonstrate that Steg-GMAN consistently outperforms both traditional and GAN-based steganographic approaches, achieving state-of-the-art security across multiple datasets.
By establishing a new benchmark in secure GAN-based steganography, Steg-GMAN advances information security by providing a more imperceptible and robust approach to concealing messages within digital media. Furthermore, its adaptive training strategy offers a versatile framework that can be extended to other GAN-based applications.
References:
[1] W. Tang, S. Tan, B. Li and J. Huang, "Automatic Steganographic Distortion Learning Using a Generative Adversarial Network," in IEEE Signal Processing Letters, vol. 24, no. 10, pp. 1547-1551, Oct. 2017, doi: https://dx.doi.org/10.1109/LSP.2017.2745572.
[2] J. Yang, D. Ruan, J. Huang, X. Kang and Y. -Q. Shi, "An Embedding Cost Learning Framework Using GAN," in IEEE Transactions on Information Forensics and Security, vol. 15, pp. 839-851, 2020, doi: https://dx.doi.org/10.1109/TIFS.2019.2922229.
[3] W. Tang, B. Li, M. Barni, J. Li and J. Huang, "An Automatic Cost Learning Framework for Image Steganography Using Deep Reinforcement Learning," in IEEE Transactions on Information Forensics and Security, vol. 16, pp. 952-967, 2021, doi: https://dx.doi.org/10.1109/TIFS.2020.3025438.
[4] B. Li, M. Wang, J. Huang and X. Li, "A new cost function for spatial image steganography," 2014 IEEE International Conference on Image Processing (ICIP), Paris, France, 2014, pp. 4206-4210, doi: https://dx.doi.org/10.1109/ICIP.2014.7025854.
[5] D. Huang, W. Luo, M. Liu, W. Tang and J. Huang, "Steganography Embedding Cost Learning With Generative Multi-Adversarial Network," in IEEE Transactions on Information Forensics and Security, vol. 19, pp. 15-29, 2024, doi: https://dx.doi.org/10.1109/TIFS.2023.3318939.
